Sunday, May 10, 2015
Created file in different versions of MS Office

Initially, I wasnt satisfied with this modify. Im usually traditional about well-known and recognized computer file formats--especially those reinforced by a great many application venders--and dont want them to be modified. And almost everyone at work application business has been assisting .doc and .xls for years.
But Microsoft company did an outstanding job creating the conversion as easy as possible, and guaranteeing that both the old and the new types would stay understandable. (If anyone believes Im a shill for Microsoft company, I recommend they study Why you should not update to Microsoft windows 8.)
Youll have no problems running an old .doc computer file into a contemporary edition of Term. (Im talking about Term particularly for comfort benefit. Everything I say here also works for Succeed and PowerPoint.) Just double-click the computer file and it will start.
You can also preserve a .doc computer file, so that people using mature editions can study it. In the Save As discussion box, simply choose the Save as pull-down selection and choose Term 97-2003 Records (*.doc).
Previous editions of Term were published without information of the .doc x structure, so you cant anticipate them to study it without a little help. But the help is there. If youre using Workplace 2003 (or even Workplace 2002 or 2000), obtain and set up the Microsoft company Workplace Interface Package for Term, Succeed, and PowerPoint File Formats. Youll be able to start, modify, preserve, and make the more recent x types.
And yes, the more recent types have their benefits For one thing, the information are small, since the x types have loss less pressure developed in. In common, .docx information are about half the dimension .doc information with the same content, and Ive seen some less than a one fourth of the dimension, creating it simpler to email or back-up the information. According to Microsoft company, theyre also more protected and recoverable, although I havent seen proof of this with my own sight.

Yes, a .docx computer file is really a .zip database (I informed you it was compressed). Most of what you find inside are .xml files--another start conventional. That research will also work on .xlsx and .pptx information.
After youre done testing, dont ignore to modify the expansion back to .docx.
Every well-known and effective application consistently produces more recent editions, usually every season in the case of well-known applications. When Microsoft® produces a program of any office program, they provide frequent up-dates so they do not need to launch one every season. When a significant renovation of the Microsoft company Office® Suite happens in which it is more recent, customized, prolonged, and with a more contemporary GUI (which contains the Microsoft® Term written text editor), the changes are not only developed to the program but also include computer file type and structure changes. This is because the new papers types are developed in the same way as the performance of the program. However, problems may happen when trading documents published in mature editions of an program. In the actions below, you can learn how to preserve Microsoft® Term information to be suitable with previously editions.
Instructions:
Start the Microsoft® Term 2010 program.
Open the computer file in which you want to “re save,” or make a new papers.
Click on the “File” tab in the main routing bar.
Choose “Save As” or “Save” for a recently developed papers.
Write the name of the papers in the “File name” box.
From the “Save as type” drop-down, select the preferred edition (usually “Word 97-2003 Document [*.doc]” version).
Click the “Save” key to preserve in an previously edition of Microsoft® Term.
Thursday, February 26, 2015
10 Principles Of Effective Web Design Smashing Magazine
- Link to 10 Principles Of Effective Web Design

"(Web) Users:
- Appreciate quality and credibility!
- Don’t read, they scan!
- Are impatient and insist on instant gratification!
- Don’t make optimal choices.
- Follow their intuition.
- Want to have control (Source)."
No wonder SCORM does not appeal to learners (and educators) (above 5 years old)! Below 5 years old? Only because they think it is some kind of worm, or it sounds cool!
10 PRINCIPLES OF EFFECTIVE WEB DESIGN?
- Don’t make users think!
- Don’t squander users’ patience!
- Manage to focus users’ attention!
- Strive for feature exposure!
- Make use of effective writing!
- Don’t be afraid of the white space!
- Strive for simplicity!
- Communicate effectively with a “visible language”!
- Conventions are our friends!
- Test early, test often!
If this does not make any sense, click here to read between the lines.
SMASHING MAGAZINE? "Founded in September 2006, Smashing Magazine delivers useful and innovative information for designers and web-developers. Our aim is to inform our readers about the latest trends and techniques in web-development. We don’t try to convince you with the quantity, but with the quality of the information we present. That’s what makes us different. In fact, we smash you with the information which will make your life easier. Really (Source)."
"Founded in September 2006, Smashing Magazine delivers useful and innovative information for designers and web-developers. Our aim is to inform our readers about the latest trends and techniques in web-development. We don’t try to convince you with the quantity, but with the quality of the information we present. That’s what makes us different. In fact, we smash you with the information which will make your life easier. Really (Source)."
MASTERMINDS?
"Smashing Magazine is maintained by Sven Lennartz, the owner of the Dr. Web Magazine and Vitaly Friedman, the creator of The Web Developer’s Handbook (Source)."
OTHER SMASHING POSTS?
The previous post on OCW collections for web designers was an amazing learning discovery. However, I am not sure if I have the time or patience to explore 60+ courses to find nuggets of learning juice relevant and useful to my learning adventure. No doubt the OCW collections have tremendous value, but for now I am simply looking for smashing articles on specific web stuff that I want to learn (Or discover by accident!). And when I discovered this Smashing Magazine, I was like, "This looks interesting! Hey, this looks even more interesting! WOW, this is the one I am looking for!" Smashing Magazine provides you with short and engaging nuggets of learning tailored to the things you really want to know (in design). They smash you with the learning juice!
To illustrate my point, here are some smashing posts (titles) discovered that I really want to explore soon:
- 170+ Expert Ideas From World’s Leading Developers
- Evolve Your User Interface To Educate Your Users
- 30 Usability Issues To Be Aware Of
- 10 Usability Nightmares You Should Be Aware Of
- 20 (Alternate) Ways to Focus on Users
- White Space and Simplicity: An Overview
- 25 Mind-Blowing Gadgets
- Award-Winning Newspaper Designs
- PDF: Five Smashing Wisdom Treasures
- Google PageRank: What Do We Know About It?
- Google AdSense: Facts, FAQs and Tools
- 45 More Excellent Blog Designs
- Monday Inspiration: Innovative Designs and Devices
- Monday Inspiration: User Experience Of The Future
- Monday Inspiration: 3D-Experience in Flash
- 65 Excellent Flash Designs
Absolutely SMASHING! So, if you are looking for a course on web design stuff, you have 60+ courses to explore, and if you want to find some short and juicy learning nuggets on web design, Smashing Magazine is a great alternative. Mix formal and informal learning resources and you might just have a smashing learning experience :)
Thursday, February 19, 2015
Installation of Pentaho 5 0 1 CE in windows 7 changes made from previous version
First of all, Id like to thank you to the web details team for the efforts they kept in bringing up the powerful analytical engine(BA server).
The home page itself make you to stick with BA server where you can enter into the server with "admin" and "password" as the default credentials.. Yes, "joe" user is no more but he left with the same password to log into BA server.
There will be NO more admin console ... Now it is very easy and developer friendly to navigate in one console(User Console) to give data base connections and new roles for new users..
A lot of stuff included in the home page itself, giving the blogs links, books on different tools of pentaho family. In a single word I can say , All the stuff related to Pentaho at a single place. A BI developer like me can reduce the time for developing reports, dashboards , jobs.
Market place for installing C-Tools and the installed plug-ins list drop down is one of the good ideas of the team.
As quick as Pentaho released its CE 5.0.1 , I just downloaded and trying to explore the new look and navigating from all the menus, reports, connection places and etc.
Its very easy to install the pentaho CE BA now in windows...
Installation procedure :
1) Down load the software as a .zip file using this link .
2) Unzip it in your fav folder
3) Click on start-pantaho.bat file
Home page :
NOTE: path and class path for java must be set before the installation.
C program to copy the contents of one file into another
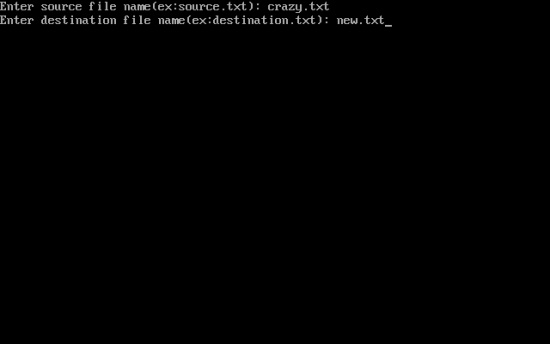
#include<stdio.h>
#include<conio.h>
#include<stdlib.h>
void main()
{
FILE *fp1,*fp2;
char ch,*f1,*f2;
clrscr();
printf("Enter source file name(ex:source.txt): ");
scanf("%s",f1);
printf("Enter destination file name(ex:destination.txt): ");
scanf("%s",f2);
fp1=fopen(f1,"r");
fp2=fopen(f2,"w");
if(fp1==NULL||fp2==NULL)
{
printf("File could not open!!");
exit(0);
}
while((ch=getc(fp1))!=EOF)
putc(ch,fp2);
fclose(fp1);
fclose(fp2);
}
Wednesday, February 18, 2015
C program to find the sum of series 1 2 4 5 7 8
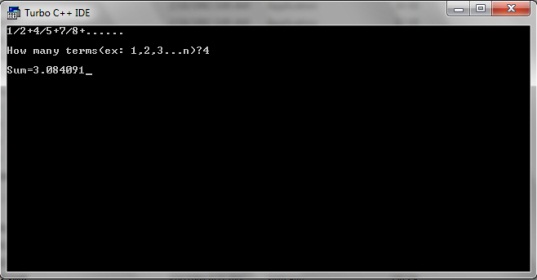
How many terms(ex: 1,2,3...n)?");
Sum=%f",sum);
Limits Of Legality
 |
| RAT Limits Of Legality |
Anyone serious about learning hacking should make sure to go through all the relevant laws in their jurisdicitions. For those who are not so serious, it is even more important. Simply goofing around may be enough to rack up a hefty fine, probation or even a sentence. In germany, for example, simply owning a tool that can be used for hacking, is a crime. One may actually be convicted for downloading a freaking app. In the same country, a professional penetration tester or a 12 year old may be regarded as criminal hackers just because s/he downloaded Cheat Engine (Im serious) or BackTrack OS. This is not to single out Germans but to show that imperfect laws still exist in almost every countrys constitution (Germans, dont worry. I have a lot more laws to insult from all over the world. But well leave these for another day) This problem depends on your geography only a little, but it is mostly global.
Why bother with all this legal nonsense? If youre not the type to spend your life fighting pointless politics or start protesting around to change existing laws, you need to follow them. After all, what choice do we have? Jail? Sure, why not. If you arent against something, then by definition, you support it. Anyways, lets leave politics for another website.
When it comes to hacking, no matter where you live, practically doing it means walking a fine line. But, before anything else, before the law too, you need to look after yourself and make sure you are aware of every possible consequence of performing a hack or anything even remotely related. From running batch files, which can wreck your computer to hacking a schools server which can get you expelled to leaking NSA secrets which can open the eyes of the world, you need to tread carefully. When it comes to hacking, there is no universal definition of right and wrong. Its different for the government, its different for the anonymous hackers group and it will be different for you and me. While were on this, you may have heard about the "criminal" anonymous hacktivist group and their "illegal" and "unethical" activities in the news and media somewhere. Take a wild guess, whos definition of right or wrong does the media follow?.. The obvious can be surprising. Change your viewpoint and you can change your world.
Coming back to the limits of legality, what all is legal for an average joe who wants to learn hacking? Although the exact answer will depend on your address (another bug in the matrix..), there are some general things you should keep in mind while learning and carrying out different hacking techniques, no matter where you live. These are not only to keep you out of jail but also to protect you from yourself. Since our lives will just keep on getting more and more dependent on technology, hacking is no longer just about hacking. Plus, it wont hurt to double check what youre doing wont get you in trouble.
•Know what youre doing.
Whatever the hacking method youre trying to do, it can never hurt to know a little more than what you need. You just might end up saving yourself a lot of trouble. Just one misplaced command in a batch file virus could spell disaster. As a rule of thumb: If you dont know what youre doing, dont do it. In the world of hacking, its easy to get carried away, specially when you try out something new, it works and you want more. Skipping the learning phase and moving straight to the doing phase is what turns potential hackers into script kiddies. In professional penetration testing, a small mistake in typing the IP address may result in you "hacking" into a whole different company on the other end of the globe. Clearly, they may not care about the difference between "pentesting" and "hacking" and your boss will find a lawsuit waiting to greet him. Actually, typos dont really lead to lawsuits. The point is, a big firm can probably get away with a little mistake. You cant. If you hack into some server or network where you dont have permission, there is no justification for what youre doing there (if youre caught). Now THIS, looks more like lawsuit material.
•Know the consequences of what youre doing.
This is an extension of the previous point. Before performing any hack, you should always try to visualize every step. See it in your mind, what all you need to do and what exactly is the expected outcome. You should try to avoid involving someone elses property or devices when learning hacking. If you stick to what you know, you should always be able to predict what will happen. That will leave only typos and genuine errors. Hacking is not all that dangerous and unpredictable if you know what youre doing.
•Dont hack anyone without their knowledge.
It may be only a fun little trick for you, but for the other person it could be an invasion of privacy or perhaps a massive violation of all the trust they put in you, for the more dramatic ones. Not all hacking techniques can be tried on yourself for practice. Most can, but still some like those involving networking need more systems. Its great if you can find a willing and trust-worthy friend and try hacking eachother for learning. If you ever consider trying larger and more elaborate hacks, taking written permission from all the involved parties is a good idea. For example (students), asking your computer teacher permission to simulate a DDOS attack in the computer lab, or perhaps the local cyber cafe. Another example, hacking public (protected) WiFi networks is illegal. You could try knocking on your neighbours door and advising them to switch over from WEP to WPA. This is what puts the "ethical" in "ethical hacker" and the chances of them giving you the new password by simply asking also increase.
•Know when to stop.
Companies hire penetration testing firms to check the security of their networks but almost always want them to stay away from private and confidential information, even if they have access. If someone were able to "guess" the facebook password of someone, it doesnt give them the right to exploit their ability without regard for anyone else. With each passing moment, our lives are getting more and more integrated with technology making it extremely important to know when to stop.
•Know the law.
In normal hacking, you will probably never need to be worried about legal trouble but it wont hurt to double check. To be extra sure, you can google up the constitution of your country or search for relevant laws regarding hacking.
Thats pretty much all a beginner hacker needs to know about the legal side of hacking. Once again, anything you do on your own computer that affects nobody else is usually safe (for others). As the world is increasingly interconnected, everyone shares the responsibility of securing cyberspace. Hence, it is better to be despised for anxious apprehensions, than ruined by superficial security (a little bit).
Tuesday, February 17, 2015
Explain Basic Structure of C Programs

Documentation Section
This section consists of comment lines which include the name of programmer, the author and other details like time and date of writing the program. Documentation section helps anyone to get an overview of the program.Link Section
The link section consists of the header files of the functions that are used in the program. It provides instructions to the complier to link functions from the system library.Also Read: List of all useful Turbo C++ keyboard shortcuts
Also Read: How to create your own Header Files in C/C++?
Definition Section
All the symbolic constants are written in definition section. Macros are known as symbolic constants.Global Declaration Section
The global variables that can be used anywhere in the program are declared in global declaration section. This section also declares the user defined functions.main() Function Section
It is necessary have one main() function section in every C program. This section contains two parts, declaration and executable part. The declaration part declares all the variables that are used in executable part. These two parts must be written in between the opening and closing braces. Each statement in the declaration and executable part must end with a semicolon (;). The execution of program starts at opening braces and ends at closing braces.Also Read: What are advantages and disadvantages of C language?
Also Read: How to Write and Run C/C++ Programs in Ubuntu (Linux)
Subprogram Section
The subprogram section contains all the user defined functions that are used to perform a specific task. These user defined functions are called in the main() function.Monday, February 16, 2015
Exporting CDE dashboard to pdf the usage of PRD for CDE
Exporting chart components as images to pdf in pentaho CDE - Simple Example
Here is the functionality of exporting CDE chart components to pdf file using PRD.
Environment :
C-Tools : V13.09
Pentaho Server : 4.8
Database : foodmart (jasperserver default database)
Web browser : Mozilla Firefox
NOTE : This post is specific to export chart component(s) to pdf but not the table component you are seeing in the images in this post.
What you can learn from this example ?
1) Make use of button component for exporting dashboard charts to PDF.
2) What is CGG component ? How you can make use of CGG component in exporting charts as images to PDF ?
3) How you can use PRD(.prpt) tool to export the images to PDF.
4) How to pass parameters in the URL when you export the dashboard charts as images in pdf file.
Example :
1) Lay out section
* Design and develop your dashboard as per your requirement.
* Find the image below

(Talking about chart only)
* Give database connections and write a simple query which gives meaning full visualization.
* For example:
SELECT fname,customer_region_id FROM customer LIMIT 6
3) Components section
i) Take button component from others give place holder in layout section as shown in first image
ii) Give:
Name : ExportToPDF
Label: ExportToPDF
HtmlObject: ExportPDF
Expression :
Write below code:
function sendParameter(scene){
var url=http://localhost:8085/pentaho/content/reporting/reportviewer/report.html?solution=CDEExploring&path=%2FDevelopement%2FExporting&name=ExportPDF.prpt&locale=en_US;
window.location=url
}
Code image is shown below.

Well come to know from where we are taking the code above seen in image.
Here PRD(Pentaho Report Designer) comes into picture to export the CDE dashboard charts to pdf or any other format.
Below steps are the work around with CGG(Community Graphics Generator) & PRD
For CGG complete reference find Pedros blog here
From web details http://www.webdetails.pt/ctools/cgg.html
Steps :
1) Preview your dashboard
2) Press shift+G .. you will find pop up of CGG and URL generated for the charts in your dashboard.
i.e., once you click shift+G , pentaho Engine generates .js files related to that particular chart(s).
3) Take that URL and paste in any web browser address bar (Mozilla is preferable).
itll generate the images of that particular .js file(i.e., for that particular URL).
4) Your browser directly doesnt know from where the data is coming.. so you need to provide the user name and password of your pentaho(for instance: if you run pentaho on joe and password for 4.8 BA server you need to give these details)
Example:
http://localhost:8085/pentaho/content/cgg/Draw?script=/CDEExploring/Developement/Exporting/DashboardExport_BarChart.js&outputType=png&userid=joe&password=password
Note that if your chart in the dashboard is using any parameter you need to pass them by adding to the url
Syntax for adding parameters : ¶m_name=parameter_value
Example : ¶m_country=USA
5) Now, open PRD and save the .prpt file
6) Drag and drop image to "Report Header"(Preferable band) and double click on it. Give the same URL for that image, also adjust height ,width of the image. You will find the same image that you seen in web browser here in PRD image component.(If you wont find you missed some where in the development).
7) Now publish the .prpt file to Pentaho BA server.. [the folder which you are keeping your dashboards is preferable to publish your report]
[the same way you publish schema]
8) See the preview of the report.. there you can export generated output to different formats.. lets say pdf, xlx, html and etc.
9) After seeing the preview of the .prpt file, open the same using" Open in New window" which generates the URL for that..
10) Give the same URL in Button component " Export" property which you can find in step 3(Components section).
Thats it.. you have done with exporting chats of dashboard to pdf and other formats..
Find the images below for the same
step 1 & 2 image:

step 3 and 4 image:

Step 5 and 6 image:

Step 7 images:

Step 10 output:

Reference :
http://www.ambientbi.co.uk/?p=357
Hoping that this tutorial is helpful also hoping that there will be direct export functionality in pentaho CDE in upcoming releases from pentaho(Pedro).
Suggestions/Improvement of post are welcome in comments box :)
Fill Colour of bar s based on a condition in Pentaho CDE
Sample Scenario :
Print bar color as red when bar value <=2000
Print bar color as green when bar value >2000 and <10000
Print bar color as black when bar value>=10000
Scenario 2 :
When representing -Ve values on charts .. this kind of representation is preferable.
Code is Taken from Reference links :
function changeBars(){
var cccOptions = this.chartDefinition;
// For changing extension points, a little more work is required:
var eps = Dashboards.propertiesArrayToObject(cccOptions.extensionPoints);
// add extension points:
eps.bar_fillStyle = function getColor(){
var val = this.scene.vars.value.value;
if(val > 0 && val <= 5000){
return red;
}
else if(val > 5000 && val <= 50000){
return green;
}
else{
return black;
}
};
// Serialize back eps into cccOptions
cccOptions.extensionPoints = Dashboards.objectToPropertiesArray(eps);
}
NOTE : I have tried directly in Extension points but it did not work.
Sample output 1 :

function changeBars(){
var cccOptions = this.chartDefinition;
// For changing extension points, a little more work is required:
var eps = Dashboards.propertiesArrayToObject(cccOptions.extensionPoints);
// add extension points:
eps.bar_fillStyle = function getColor(){
var val = this.scene.vars.value.value;
if(val == 26297.2900){
return black;
}
else{
return blue;
}
};
// Serialize back eps into cccOptions
cccOptions.extensionPoints = Dashboards.objectToPropertiesArray(eps);
}

References :
http://translate.google.com/translate?&ie=UTF-8&sl=&tl=en&u=http://www.redopenbi.com/group/ctools/forum/topics/colores-en-bar-chart?commentId=2400100%3AComment%3A103280&xg_source=activity&groupId=2400100%3AGroup%3A73260
OR
http://www.redopenbi.com/group/ctools/forum/topics/colores-en-bar-chart?commentId=2400100%3AComment%3A103280&xg_source=activity&groupId=2400100%3AGroup%3A73260
OR
http://forums.pentaho.com/showthread.php?150582-Bar-chart-colors-dynamically-changed-based-on-data-value-Along-with-JavaScript-vars
C Program to print table of any number
#include<iostream.h>
#include<conio.h>
void main()
{
clrscr();
int i,n;
cout<<"Enter a ny number:";
cin>>n;
cout<<"
";
for(i=1;i<=10;++i)
cout<<" "<<n<<"*"<<i<<"="<<n*i<<"
";
getch();
}
Sunday, February 15, 2015
C Program to Count no of alphabates digits and spaces present in a file STORY TXT

#include<fstream.h>
#include<conio.h>
void main()
{
clrscr();
ifstream fin("STORY.TXT");
char ch;
int i,a=0,s=0,d=0;
while(fin)
{
fin.get(ch);
i=ch;
if(i>63&&i<91||i>96&&i<123)
a++;
else
if(ch== )
s++;
else
if(i>47&&i<58)
d++;
}
cout<<"No. OF Alphabates:"<<a;
cout<<"
No. Of Digits:"<<d;
cout<<"
No. Of Spaces:"<<s;
getch();
}
Master Of SEO Series Part2 Bangla

Download Now Part2 Chap1
Download Part 1
Saturday, February 14, 2015
C program to count number of words in a string

#include<stdio.h>
#include<conio.h>
void main()
{
int i,words=1;
char str[100];
clrscr();
printf("Enter a string:");
gets(str);
for(i=0;str[i]!=
Java Program to Find Intersection of two Arrays
Also Read: Java Program to Find Union of two Arrays
Java Program to Find Intersection of two Arrays
import java.util.Scanner; //import Scanner class in our programclass demo
{
public static void main(String...s)
{
int i,j,n1,n2;
Scanner sc=new Scanner(System.in); //used to read from keyboard
System.out.print("Enter number of elements of first array:");
n1=sc.nextInt();
System.out.print("Enter number of elements of second array:");
n2=sc.nextInt();
int a1[]=new int[n1];
int a2[]=new int[n2];
System.out.print("
Enter elements of first array in ascending order:");
for(i=0;i<n1;++i)
a1[i]=sc.nextInt();
System.out.print("
Enter elements of second array in ascending order:");
for(i=0;i<n2;++i)
a2[i]=sc.nextInt();
i=j=0;
System.out.print("
Intersection of Arrays: ");
while(i<n1&&j<n2)
{
if(a1[i]<a2[j])
i++;
else
if(a2[j]<a1[i])
j++;
else
{
System.out.print(a1[i]+" ");
i++;
j++;
}
}
}
}

C Program to Print an Alphabet from A to L of s in Capital Letter

#include<iostream>
using namespace std;
int main()
{
int i,j,k=1;
char ch;
cout<<"Input an Alphabet in capital letters that you want to print:";
cin>>ch;
cout<<"
";
switch(ch)
{
case A:
cout<<" ";
for(i=1;i<=40;++i)
{
for(j=0;j<=22;++j)
{
if(i==1||i==2||i==21||i==20)
cout<<"*";
else
{
if(j==0||j==20)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
case B:
cout<<" ";
while(k<=2)
{
for(i=1;i<=9;++i)
{
for(j=0;j<=i;++j)
{
if(j==0||j==i)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
}
for(i=1;i<=10;++i)
{
if(i==1||i==10)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
for(i=1;i<=10;++i)
{
if(i==1||i==10)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
for(i=9;i>=1;--i)
{
for(j=0;j<=i;++j)
{
if(j==0||j==i)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
}
++k;
}
break;
caseC:
cout<<" ";
for(i=1;i<=40;++i)
{
for(j=0;j<=22;++j)
{
if(i==1||i==2||i==39||i==40)
cout<<"*";
else
{
if(j==0)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
caseD:
cout<<" ";
for(i=1;i<=18;++i)
{
for(j=0;j<=i;++j)
{
if(j==0||j==i)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
}
while(k<=4)
{
for(i=1;i<=19;++i)
{
if(i==1||i==19)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
++k;
}
for(i=18;i>=1;--i)
{
for(j=0;j<=i;++j)
{
if(j==0||j==i)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
}
break;
caseE:
cout<<" ";
for(i=1;i<=39;++i)
{
for(j=1;j<=20;++j)
{
if(i==1||i==2||i==20||i==21||i==38||i==39)
cout<<"*";
else
{
if(j==1)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
caseF:
cout<<" ";
for(i=1;i<=40;++i)
{
for(j=1;j<=20;++j)
{
if(i==1||i==2||i==18||i==19)
cout<<"*";
else
{
if(j==1)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
caseG:
cout<<" ";
for(i=1;i<=25;++i)
{
for(j=1;j<=20;++j)
{
if(i==1||i==2)
cout<<"*";
else
{
if(j==1)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
for(i=1;i<=10;++i)
{
for(j=1;j<=20;++j)
{
if(i==1||i==2)
{ if(j==1||j==14||j==15||j==16)
cout<<"**";
else
cout<<" ";
}
else
{
if(i==9||i==10)
cout<<"*";
else
{ if(j==1||j==18)
cout<<"**";
else
cout<<" ";
}
}
}
cout<<"
";
}
break;
caseH:
cout<<" ";
for(i=1;i<=40;++i)
{
for(j=1;j<=21;++j)
{
if(i==20||i==21)
cout<<"*";
else
{
if(j==1||j==19)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
caseI:
cout<<" ";
for(i=1;i<=40;++i)
{
for(j=1;j<=30;++j)
{
if(i==1||i==2||i==39||i==40)
cout<<"*";
else
{
if(j==15)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
caseJ:
cout<<" ";
for(i=1;i<=30;++i)
{
for(j=1;j<=28;++j)
{
if(i==1||i==2)
cout<<"*";
else
{
if(j==14)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
for(i=1;i<=10;++i)
{
for(j=1;j<=15;++j)
{
if(i==10||i==9)
cout<<"*";
else
{
if(j==1||j==13)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
caseK:
cout<<" ";
for(i=20;i>=1;--i)
{
for(j=0;j<=i;++j)
{
if(j==0||j==i)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
}
for(i=1;i<=20;++i)
{
for(j=0;j<=i;++j)
{
if(j==0||j==i)
cout<<"**";
else
cout<<" ";
}
cout<<"
";
}
break;
caseL:
cout<<" ";
for(i=1;i<=40;++i)
{
for(j=1;j<=25;++j)
{
if(i==39||i==40)
cout<<"*";
else
{
if(j==1)
cout<<"**";
else
cout<<" ";
}
}
cout<<"
";
}
break;
}
return 0;
}
C Program for Implementation of Circular Queue Using Array
#define MAX 10
typedef struct Q
{
int R,F;
int data[MAX];
}Q;
void initialise(Q *P);
int empty(Q *P);
int full(Q *P);
void enqueue(Q *P,int x);
int dequeue(Q *P);
void print(Q *P);
void main()
{
Q q;
int op,x;
initialise(&q);
do
{
printf("
1)Insert
2)Delete
3)Print
4)Quit");
printf("
Enter Your Choice:");
scanf("%d",&op);
switch(op)
{
case 1: printf("
Enter a value:");
scanf("%d",&x);
if(!full(&q))
enqueue(&q,x);
else
printf("
Queue is full !!!!");
break;
case 2: if(!empty(&q))
{
x=dequeue(&q);
printf("Deleted Data=%d",x);
}
else
printf("
Queue is empty !!!!");
break;
case 3: print(&q);break;
}
}while(op!=4);
}
void initialise(Q *P)
{
P->R=-1;
P->F=-1;
}
int empty(Q *P)
{
if(P->R==-1)
return(1);
return(0);
}
int full(Q *P)
{
if((P->R+1)%MAX==P->F)
return(1);
return(0);
}
void enqueue(Q *P,int x)
{
if(P->R==-1)
{
P->R=P->F=0;
P->data[P->R]=x;
}
else
{
P->R=(P->R+1)%MAX;
P->data[P->R]=x;
}
}
int dequeue(Q *P)
{
int x;
x=P->data[P->F];
if(P->R==P->F)
{
P->R=-1;
P->F=-1;
}
else
P->F=(P->F+1)%MAX;
return(x);
}
void print(Q *P)
{
int i;
if(!empty(P))
{
printf("
");
for(i=P->F;i!=P->R;i=(i+1)%MAX)
printf("%d ",P->data[i]);
printf("%d ",P->data[i]);
}
}

HP Slate to run Palm WebOS instead of Windows 7
The latest Good E-Reader News has the HP Slate quite possibly be running the Palm Web OS, after its acquisition of Palm for 1.2 Billion Dollars.
On Wednesday April 28th after the stock markets closed HP bought Palm which many people say is a buyout for the Palm OS. The HP Slate which has been a letdown from a hands on experience by a few tech analysts have said Windows 7 simply isn’t optimized for a “slate/tablet” style device, thought it suits netbooks and laptops just fine. After a recent hands on, with the HP Slate, many analysts are saying that Windows 7 is not the route to go for HPS success into the Slate PC market.
Most of the Higher profile Slate PC’s such as Dell, Notion Ink, Neofonie, and others have gone the Google Android route as their operating system of choice for the next generation of Slate PCS. HP was the lone company to be developing a Slate PC that functioned on the Windows 7 operating system.
HP and Palm are the perfect pairing for Slate PC computing. Palm uses its well designed iPAQ hardware to run the Palm OS, and for a change gets a competitive smart phone. The Pre and the Pixi either get re-engineered by HP into something more useful, or they fade away. Meanwhile, HP’s tablet gets an OS suitable for a portable device. Not only does HP get a great operating system that is very unique for its Slate device, it also gets around 2000 third party applications for its device in one day.
HP has long been saying it will use software to differentiate its products. Now it actually can. Owning and controlling its own OS has many benefits, starting with being able to dictate who can make applications, when the product is updated, and ensuring that the hardware and software work together as seamlessly as possible. Going with the proprietary OS will shield it from potential lawsuits or necessary licensing deals with Apple or Microsoft.
HP’s acquisition of Palm means the mobile wars extend to slate tablets: iPhone vs. Android vs. Palm, all over again.
But this acquisition isn’t strictly about phones. This is about HP’s future mobile OS. Bradley said several times HP will “invest heavily” in WebOS, and use it on slate PCs, Netbooks, and phones. HP was not ready to talk about possible time lines as to when a WebOS slate or WebOS Netbooks would be available, but said it planned to increase the $190 million Palm was spending annually on research and development.
HP has made some quasi-ok Smartphone’s in the past, but they have been based on Windows Mobile and unless HP is moving to Windows Phone 7 that line is dead in the water. HP still does have a couple of Windows Mobile Smartphone’s that are pretty decent, in terms of hardware.
With this purchase, lots of research and development will now go into the WebOS and it looks like the HP Slate will be running this operating system, has it gives them the distinction they need to be competitive in the Slate PC market, and gives them a large developer community in which to add applications.
For more breaking news on the HP Slate, subscribe to our Good E-Reader Magazine.
http://goodereader.com/blog/tablet-slates/hp-slate-to-run-palm-webos-instead-of-windows-7/
Friday, February 13, 2015
Operators Rivisited Hierarchy of Operators NOT and Conditional Operator in C
Why? Ah… it’s a bit confusing and I don’t want to ruin the next important topics due to that operator.
NOT Operator (!)
The NOT operator (!) is used to reverse the results. This operator is mainly used as a key in big complex programs. By using this operator we can reverse the condition easily. Lets try to understand it with an example.If ( !(y>6) )
In the above statement I am writing a condition that y should be lesser than or equal to 6. I can also write the same condition as
If (y<=6)
Both the statements will give the same results. You can use anyone of them.
Hierarchy of Operators
I have given the hierarchy of operators after arithmetic operators. Now we have learnt about the logical operators (AND OR NOT) too. So the new hierarchy of operators is given below.
Conditional Operators
They are also called ternary operators. As we have to use three arguments to use this operator.General form of Conditional/Ternary operator
(Expression 1 ? expression 2 : expression 3)
It is generally used to avoid small if-else statement. Remember it is not the alternative of if-else clauses. It can used at some places.
Lets try to understand it with some simple example.
if (x==10)
Y=3;
else
Y=9;
In the above we are basically checking if x is equal to 10. If condition turns true then it will assign y as 3. Otherwise it will assign y as 9. The same task can be completed using ternary operator.
Y=(x==10 ? 3 : 9);
I hope everyone will agree with the fact that above example is very much compact than the earlier version.
Another example to use ternary operators is given below.
( x > 4 ? printf ( "Value is greater than 4" ) : printf ( "Value is less than 4" ) ) ;
Nested Conditional Operator
Well nested conditional operators are used very rarely but they are good to make the program compact.A small example of nested ternary operator is given below
Small = ( x < y ? ( x > z ? 9: 10 ) : ( y > z ? 14: 16 ) ) ;
In the above example small is the variable and it will store
9 if x<y and x>z
10 if x<y and x<z
14 if x>y and y>z
16 if x>y and y<z
Sounds confusing? Well that’s why they are used rarely. But like our example, it can sometimes make the program compact.
So that’s all for decision control instructions. I recommend you to make programs and practice for at least 2 days before proceeding further. In the next tutorial I will cover an overview to loops in C programming.
C program which reads your name from the keyboard and outputs a list of ASCII codes which represent your name

#include<stdio.h>
#include<conio.h>
void main()
{
int i;
char name[50];
clrscr();
printf("Enter your name: ");
gets(name);
printf("
Character ASCII Code");
for(i=0;name[i]!=
C program to read a matrix of size mxn from the keyboard and display the same on the screen
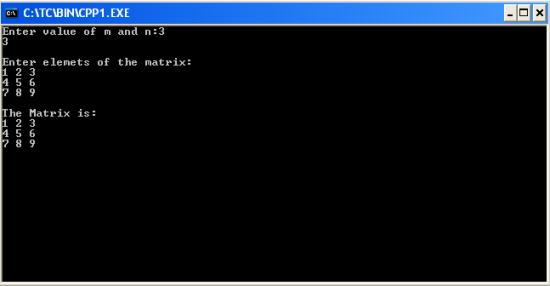
#include<iostream.h>
#include<conio.h>
void main()
{
clrscr(); //to clear the screen
int a[5][5],n,m,i,j;
cout<<"Enter value of m and n:";
cin>>m>>n;
cout<<"
Enter elemets of the matrix:
";
for(i=0;i<m;++i)
for(j=0;j<n;++j)
cin>>a[i][j];
cout<<"
The Matrix is:
";
for(i=0;i<m;++i)
{
for(j=0;j<n;++j)
cout<<a[i][j]<<" ";
cout<<"
";
}
getch(); //to stop the screen
}